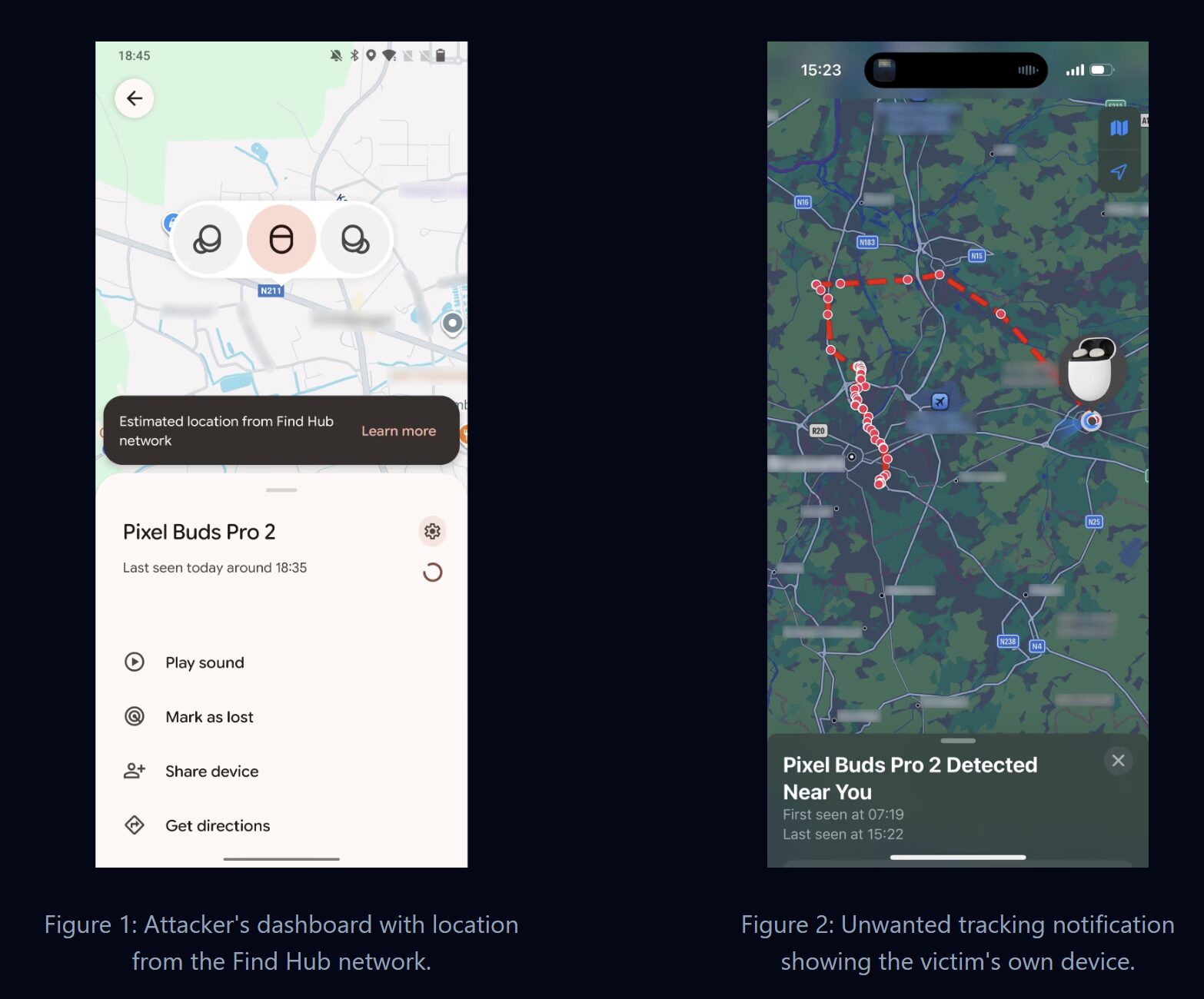
One feature I’ve always appreciated is the convenience of Google Fast Pair . It’s a magical experience to open a case and see my Xiaomi iPad 8 or Xiaomi 17 instantly pair with my earbuds. However, a massive security bombshell has just been dropped with monumental implications for this convenient feature. What’s being revealed here is the newly discovered vulnerability known as WhisperPair , which can be exploited by an attacker to silently hijack your wireless earbuds in under 15 seconds, allowing them to listen to your private conversations or track your physical location in real time.
Summary: Pair Crisis
- The threat : Attackers can bypass the pairing security of devices based on Google Fast Pair logic .
- Affected brands: Major brands such as Sony, Xiaomi, JBL, and Logitech are also included.
- The risk: Silent audio hijacking, microphone use for spying, and location tracking via Google Find Hub .
- The solution: It is essential that you manually update the firmware using the application provided by your device manufacturer.
How does WhisperPair kidnapping actually work?
«The core of the problem lies in how some of these manufacturers have chosen to implement the Fast Pair protocol . A device shouldn’t be able to establish new connections unless you’ve manually put it into ‘Pairing Mode.’ But the team discovered that many flagship devices don’t adhere to this.» With just a cheap copy of the Raspberry Pi, an attacker 14 meters away can emulate the Seeker device. In a matter of seconds, the attacker can force a connection to your Xiaomi Band 9 or headphones while you’re actively using them. They can then play audio content. However, the critical point is that the attacker can activate the microphone.
Is your location being tracked?
However, one of the worst aspects of this vulnerability is «Covert Account Linking.» If your headphones aren’t already linked to a Google account—which is very likely if you’re an iPhone user with a Sony or JBL device —a hacker can «claim» the device. They can track your location by connecting your headphones to their own account and using Google’s Find Hub (also known as Find My Device) to monitor your location. There have been reports on Reddit of people receiving «Unknown Tracker» notifications, initially mistaking them for a system bug, when in reality it allowed a stalker to track their location.
Which devices are at risk?
The 17 devices tested include some of the most popular models available. While Google has already released a fix for its Pixel Buds , other manufacturers like Xiaomi and JBL are releasing over-the-air (OTA) updates.
What’s next? How can we protect ourselves?
You can’t disable quick pairing on most accessories. It’s deeply embedded in the firmware. Your only option is to update the firmware. Open your app—whether it’s Sony Headphones Connect , JBL Headphones , or Xiaomi Earbuds —to check for a firmware update.



 Emir Bardakçı
Emir Bardakçı